Microsoft graph security api data flow Data flow: creating a bbm enterprise conference Solved in the context of the infosec program, describe the document and maintain data flow diagrams infosec
Data Flow Diagram | UCI Information Security
What is infosec and use cases of infosec? What is a data flow diagram and how to make one? Certification iso extensive agencies
Information management processes detailed in an infographic
Schematic of data information flow and customized it infrastructure toDocumenting data flow diagrams Creating an information system/data flow diagram – information securityData flow diagram data security, png, 1506x1128px, diagram, area.
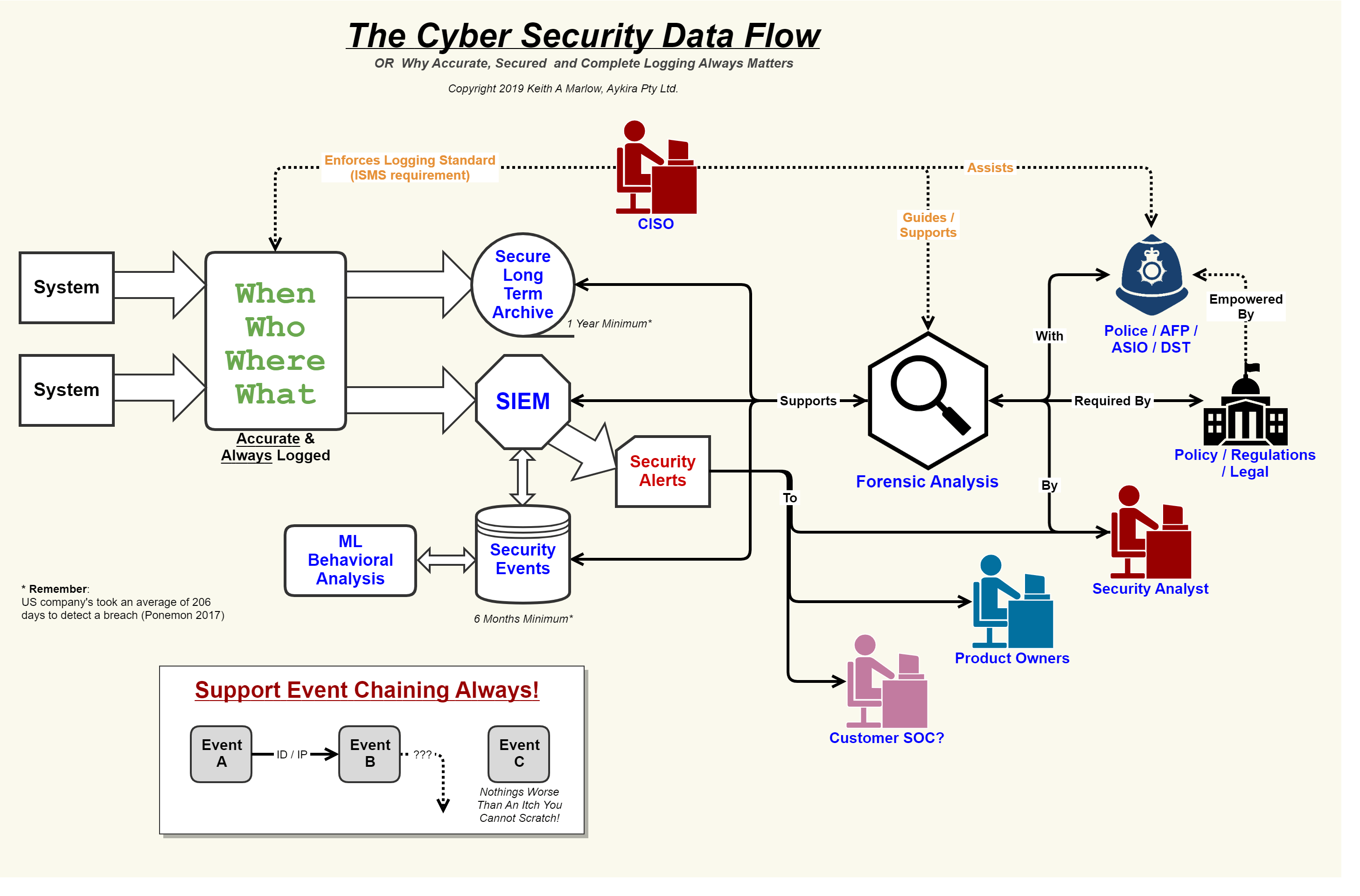
Security flow data cyber event logging diagram internet logs important why so together showing concerning events au puttingManagement information processes infographic detailed flowchart flow process data documents digital physical here gdata Data flow diagram templates to map data flowsData flow diagram.

Flow diagram data physical online types symbols lucidchart click tips marketing
Data flow and security overviewInfosec teams: document classifications at the point of creation Hướng dẫn về vẽ sơ đồ dfd online miễn phíData flow diagram.
Data flow diagram examples symbols, types, and tips5 guidelines and recommendations presented in the extended infosec 20+ online dfd design toolInfosec notes.
Network security model
A beginner's guide to data flow diagramsThe next level of information security how our clients will benefit Information securitySecurity event logging, why it is so important – aykira internet solutions.
Document management & process automationInformation flow control Protect what matters most: the dataData flow diagram showing how data from various sources flows through.
![[PDF] Solution-aware data flow diagrams for security threat modeling](https://i2.wp.com/d3i71xaburhd42.cloudfront.net/b06ef5bd909d25907ccb6f8ff32440037b492f0b/2-Figure1-1.png)
[pdf] solution-aware data flow diagrams for security threat modeling
Infosec teams: document classifications at the point of creationSecurity network diagram control computer diagrams devices networks access model solution encryption secure examples cloud example architecture conceptdraw system software What is data flow diagram?.
.








